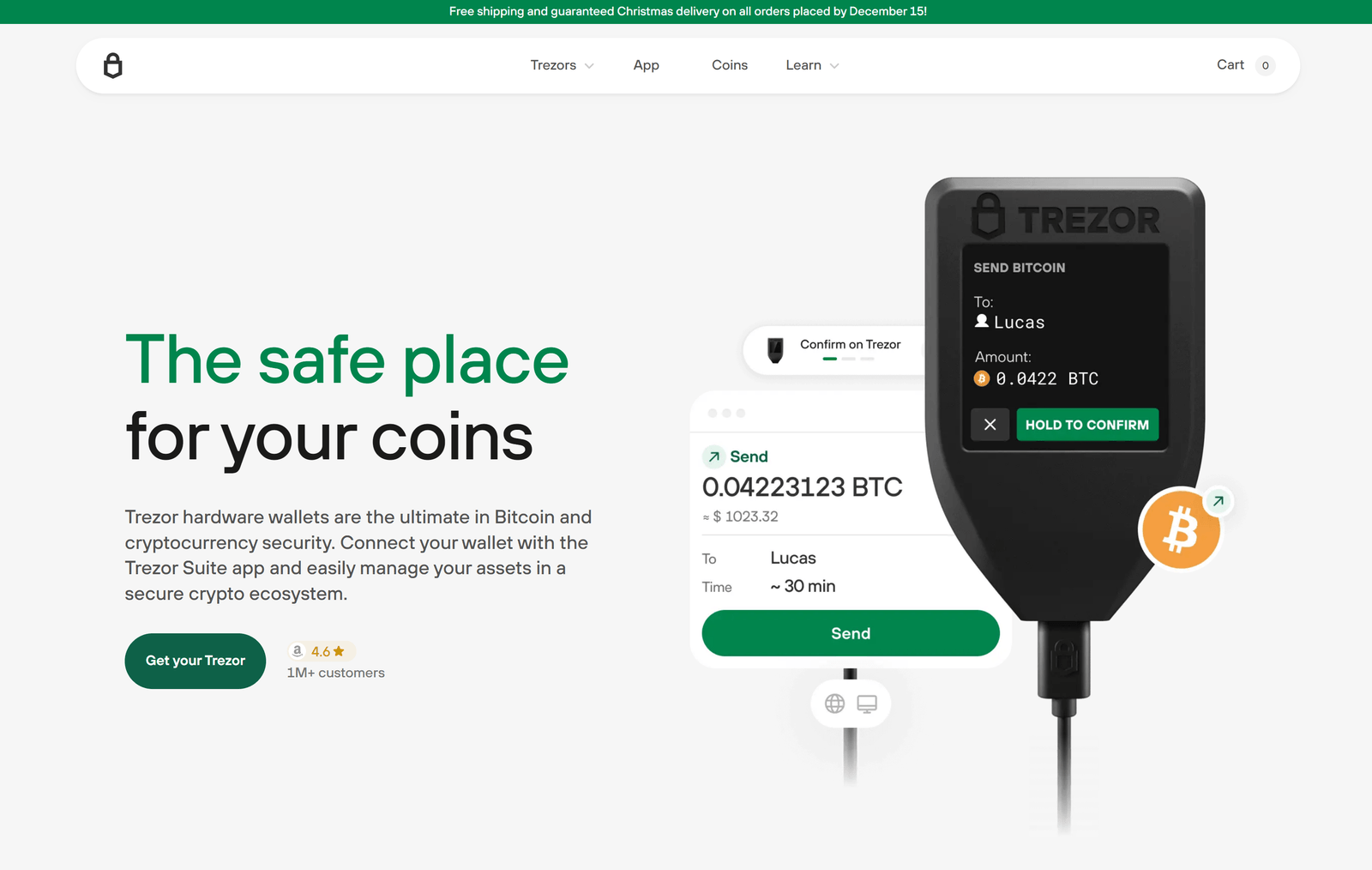
Trezor Bridge: Connecting Your Crypto Wallet Seamlessly
In the rapidly evolving world of cryptocurrency, secure and efficient access to digital assets is paramount. Among the leading names in crypto security is Trezor, a trusted hardware wallet developed by SatoshiLabs. One of the most vital components enabling a smooth interaction between the Trezor hardware wallet and a user’s browser is Trezor Bridge. This article offers an in-depth look at Trezor Bridge—its function, setup, benefits, and how it ensures a streamlined and secure experience for crypto users.
What is Trezor Bridge?
Trezor Bridge is a lightweight communication interface that acts as a secure link between your Trezor hardware wallet and your web browser. It replaces older methods such as browser extensions and is now the default connection method for Trezor devices when accessing platforms like the Trezor Suite or third-party wallets.
In simple terms, Trezor Bridge functions as a middleware application installed on your computer. Once active, it facilitates encrypted data exchange between the browser-based applications and your Trezor device, without compromising privacy or control.
Why is Trezor Bridge Important?
Modern web browsers continuously update their security models, making it difficult for browser extensions to maintain the necessary access permissions to communicate with external devices. Trezor Bridge circumvents these limitations by running locally on your machine, ensuring a direct, secure, and uninterrupted connection with your Trezor hardware wallet.
Without Trezor Bridge, users might encounter limited compatibility or be forced to rely on older, less secure methods. Bridge solves this problem with increased stability, cross-platform support, and superior privacy protocols.
Key Features of Trezor Bridge
- Seamless Connectivity Trezor Bridge enables plug-and-play connectivity for Trezor hardware wallets. Users don’t need to configure advanced settings—once installed, it runs in the background and establishes a trusted link automatically.
- Cross-Browser Compatibility Trezor Bridge supports all major web browsers such as Google Chrome, Mozilla Firefox, Microsoft Edge, and Safari, ensuring users across platforms enjoy the same secure experience.
- Secure Communication Every data exchange between the wallet and browser is encrypted. Bridge ensures no third-party interference, making it highly secure even in hostile environments.
- Open Source and Transparent Staying true to the philosophy of transparency, Trezor Bridge is open-source. Developers and users can inspect the source code, contributing to trust and accountability in the system.
- Automatic Updates The software checks for updates and installs newer versions to stay compatible with the latest browser protocols and security standards.
Installing Trezor Bridge
Setting up Trezor Bridge is straightforward and can be done in just a few steps:
- Download the latest version of Trezor Bridge from the official site https://trezor.io/start.
- Install the application by running the downloaded file (available for Windows, macOS, and Linux).
- Once installed, the Bridge runs automatically in the background.
- Connect your Trezor device via USB, open your browser, and launch Trezor Suite.
- The application will detect the Trezor hardware wallet and initiate a secure session via Trezor Bridge.
It’s essential to always download Trezor Bridge directly from the official source to avoid counterfeit software and phishing attacks.
Compatibility and Use Cases
Trezor Bridge is fully compatible with:
- Trezor One
- Trezor Model T
In addition to Trezor Suite, Bridge supports interaction with popular wallets and DeFi platforms like:
- MetaMask (with Trezor integration)
- Exodus Wallet
- Electrum
- MyEtherWallet
- MyCrypto
This versatility allows users to access a wide range of decentralized applications while benefiting from Trezor’s hardened security model.
Security Considerations
Security is the cornerstone of Trezor Bridge. Since it doesn’t require browser extensions—which have known vulnerabilities—the Bridge architecture reduces the attack surface. All communications between the Trezor device and the browser are verified, encrypted, and free from third-party logging or tracking.
Made in Typedream